
We ensure a seamless Jira deployment, configuring it to align with your business processes for optimal workflow management.
Enhance efficiency with tailored automation rules, reducing manual work and ensuring smooth task transitions.
Leverage Jira’s Agile and Scrum tools for sprint planning, backlog management, and real-time progress tracking.
Integrate Jira with essential tools like Confluence, Bitbucket, Slack, and third-party applications to create a connected ecosystem.
Gain valuable insights with customizable dashboards and reports to track team performance and project progress.
Secure your projects with customizable permissions, ensuring data privacy and access control based on user roles.
Seamlessly integrate our top-tier developers into your workflow.
Boost your team’s capabilities without the overhead of full-time hires.
Access on-demand expertise whenever you need it.

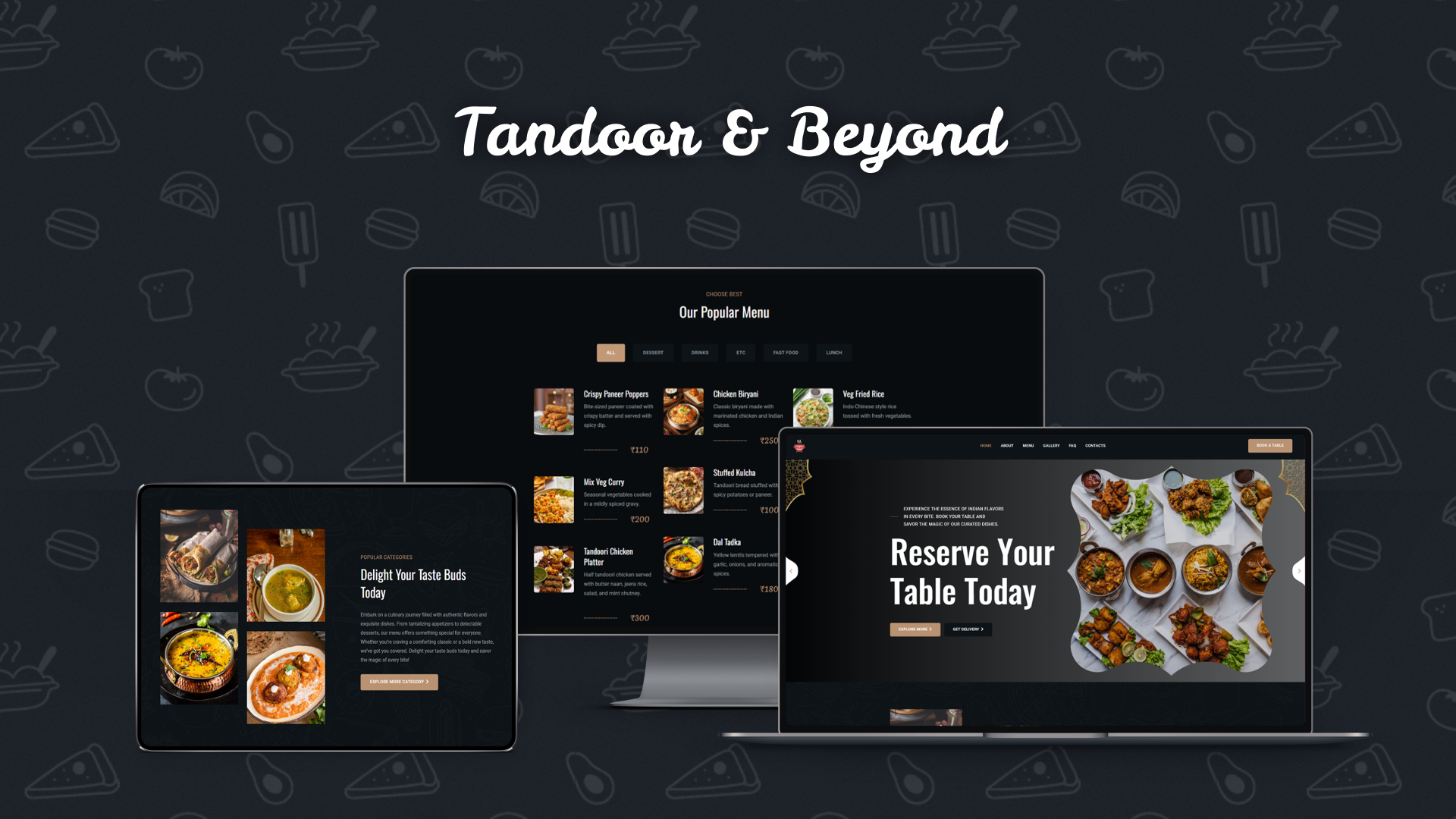
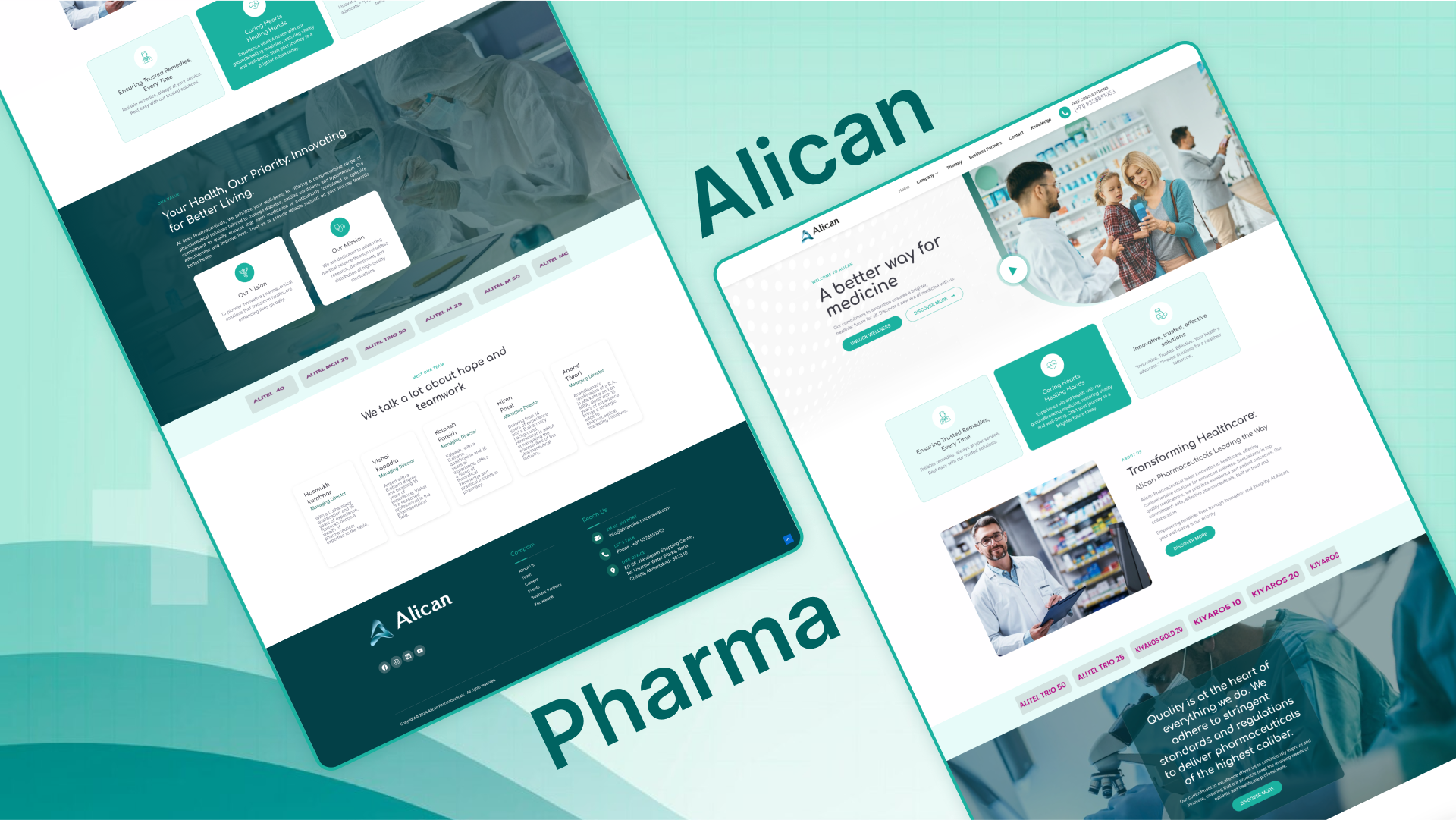

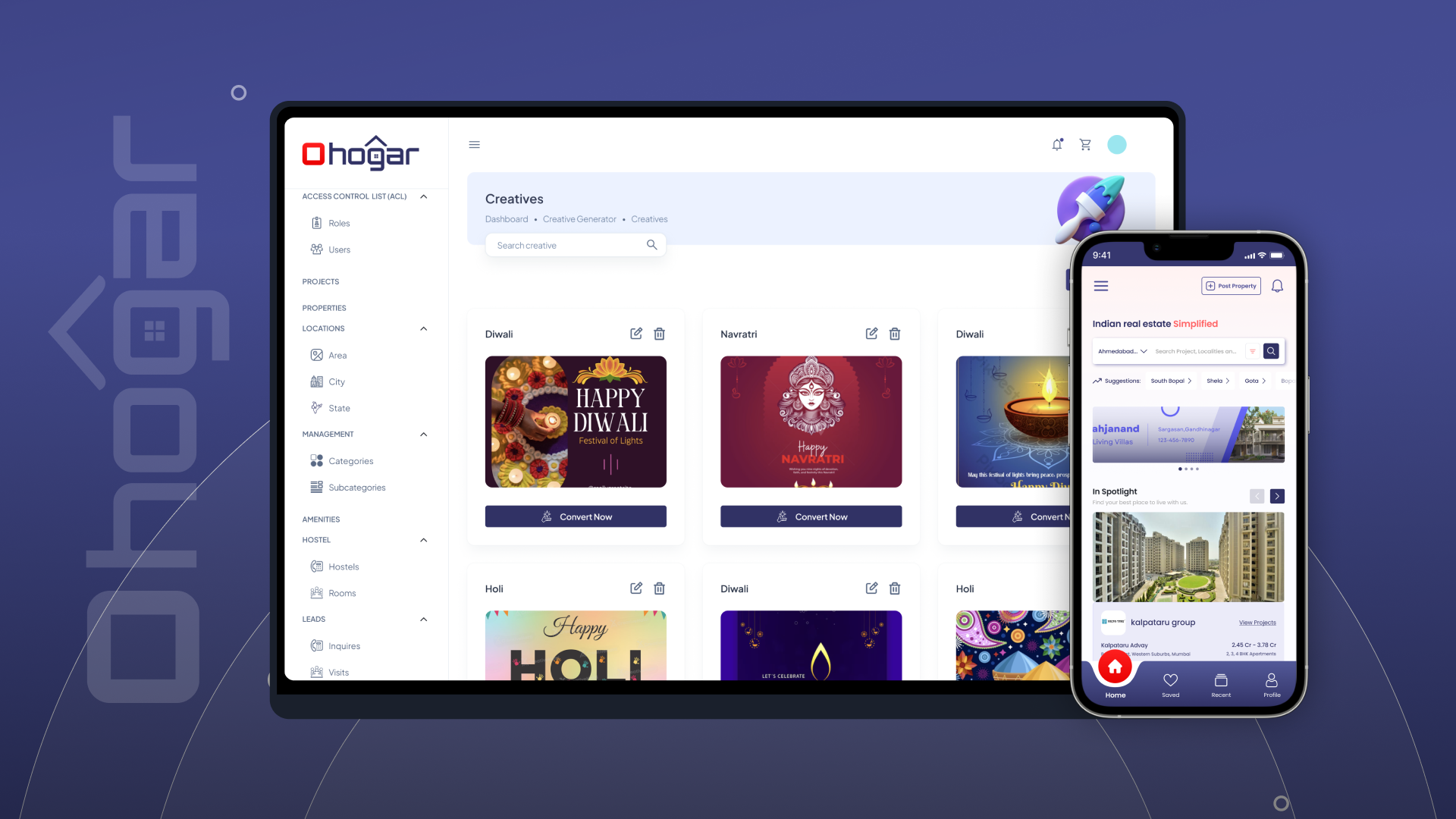
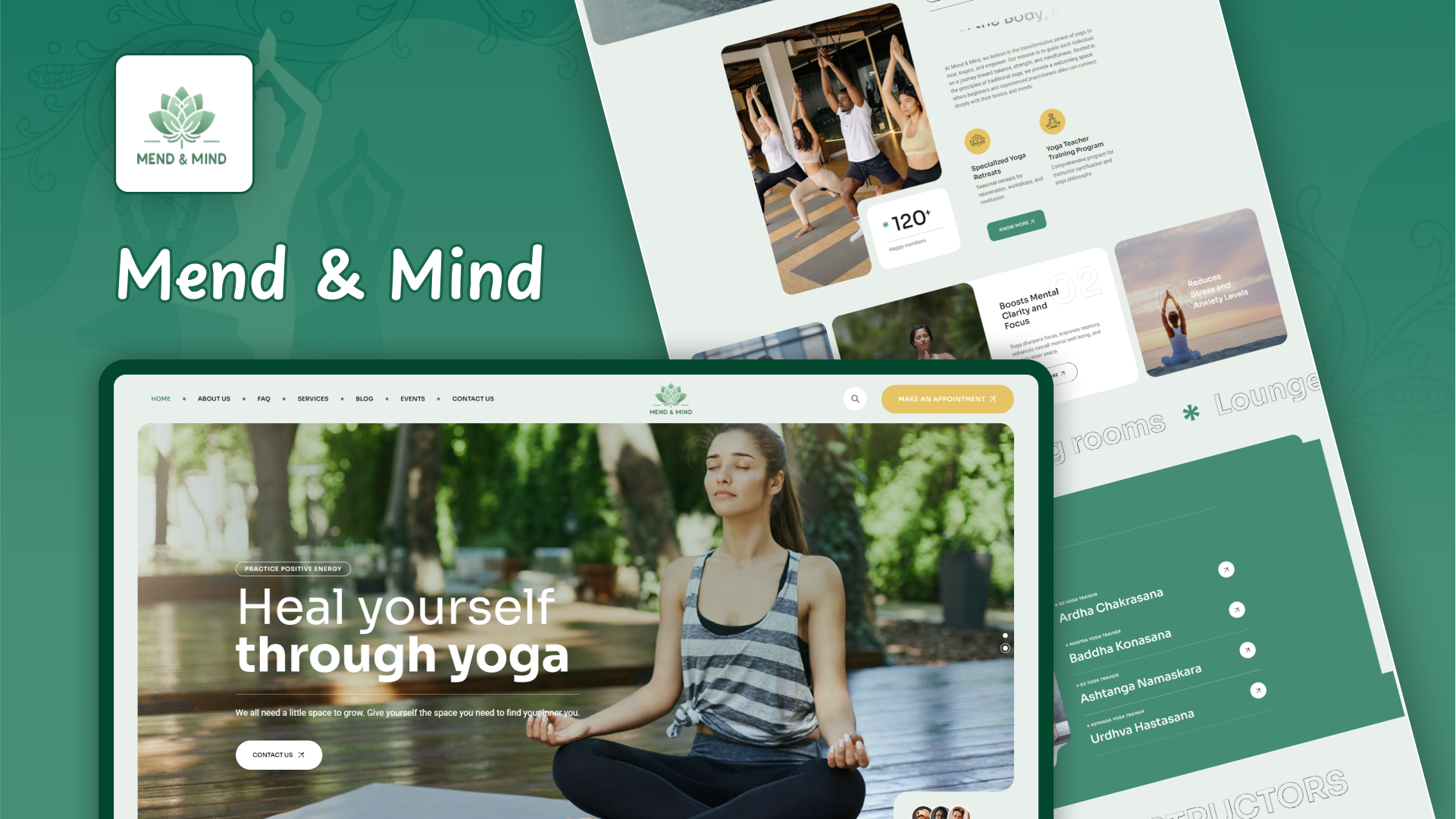















AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS services and resources for your users. It allows you to create and manage AWS users, groups, roles, and permissions.
IAM users are entities that you create to represent individuals or applications that need access to your AWS resources. Each user has a unique set of credentials (passwords, access keys) for authentication.
IAM groups are collections of IAM users. Groups allow you to manage permissions for multiple users at once by attaching policies to the group, which apply to all users within that group.
IAM roles are AWS identities with specific permissions. Roles can be assumed by users, applications, or AWS services. They are often used for granting temporary access and managing permissions across different AWS accounts or services.
IAM policies are JSON documents that define permissions. Policies specify what actions are allowed or denied on specified resources. They are attached to users, groups, or roles to control access.
IAM handles permissions using policies attached to users, groups, or roles. Permissions are defined in policies that specify allowed or denied actions on AWS resources. IAM evaluates these policies to determine access.
Multi-Factor Authentication (MFA) is an additional security layer that requires users to provide a second form of authentication (such as a code from a mobile device) in addition to their password or access key.
IAM supports cross-account access by allowing roles to be created in one AWS account and then assumed by users or services in another account. This enables secure access to resources across multiple accounts.
AWS IAM Access Analyzer helps you identify and review permissions granted to IAM roles, users, and services. It helps ensure that access is not inadvertently granted to unauthorized entities.
IAM allows you to define policies that grant or restrict permissions for AWS services. Service-specific permissions are managed by attaching policies to roles that services can assume.
All copy right reserved 2025 @CodnestX